Single Sign On (SSO) configuration
Single Sign On is configured under team settings. Selecting Enforce SSO will prevent users from logging into the platform using their username and password.
V7 supports SAML and Google Auth 2.0 as SSO protocols. Both options can be used to automatically create and add new team members, and the role which is given these new joiners is controllable via the Default Role settings.
SAML 2.0
As SAML allows control of which users are assigned to an Application within the Identify Provider; any user who is able to sign in via SAML will automatically be added to the team using the configured default role.
First, create Darwin as an application in your Identity Provider. Once the application is created, you'll need to configure an Entity ID, Assertion URL and some attributes & claims:
- Entity ID: https://darwin.v7labs.com
- Assertion URL: https://darwin.v7labs.com/api/users/authenticate/sso/saml/validate
Note on the Entity IDIf you integrated with V7 SAML before 1 November 2023; you would have set the
entity_idtov7_labs. Your integration will continue to work with this value. If you need to update to using a valid URI; first addhttps://darwin.v7labs.comas an additionalentity_idwithin the V7 application in your IdP and then contact your V7 Customer Representative to request to update theentity_idin use for your integration.
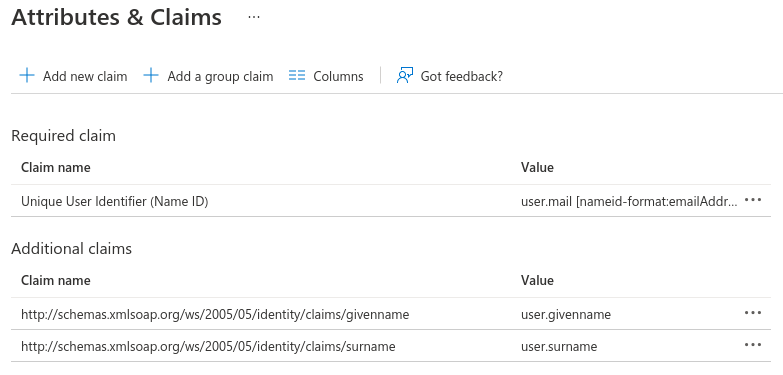
Azure Attributes & Claims
- Name ID: user.mail
- NameID format: Email address
- http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname: user.givenname
- http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname: user.surname
Okta Attrbutes & Claims
- http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname: user.firstName
- http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname: user.lastName
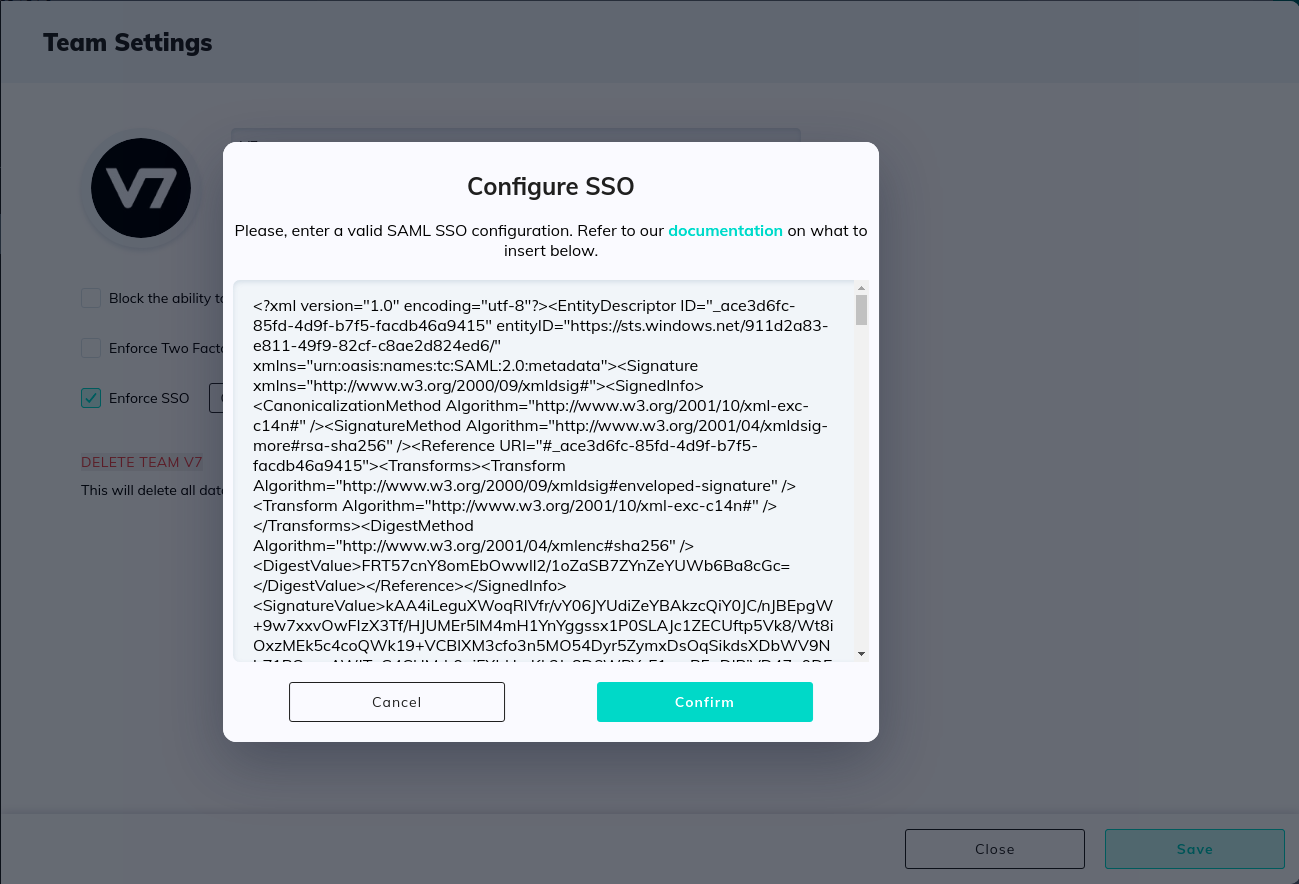
After configuring & saving the above, download the metadata file for the application. Navigate to team settings within Darwin & select Configure SSO. Paste the entirety of the metadata file into here and select Confirm:
Google Auth 2.0
In order to enable adding new users to your team automatically via Google Auth 2.0; it it possible to configure an email Business Domain. Any new sign-in from a matching email will then be added to your team.
Multiple workspacesIf you're setting up SSO For multiple workspaces under one parent team, then additional setup will be required.
Check out our guide here on SAML Configuration across multiple workspaces.
Updated 6 months ago
